Join PlusPlus Today!
Capture, index, and surface expertise—effortlessly.
About
Operationalize your expert’s knowledge
Enable your people to easily capture and release organizational knowledge using tools they already use.
Features
Build Blended Learning Programs with Ease

Live Events
Supercharge your workshops and classes with virtual and in-person live events.
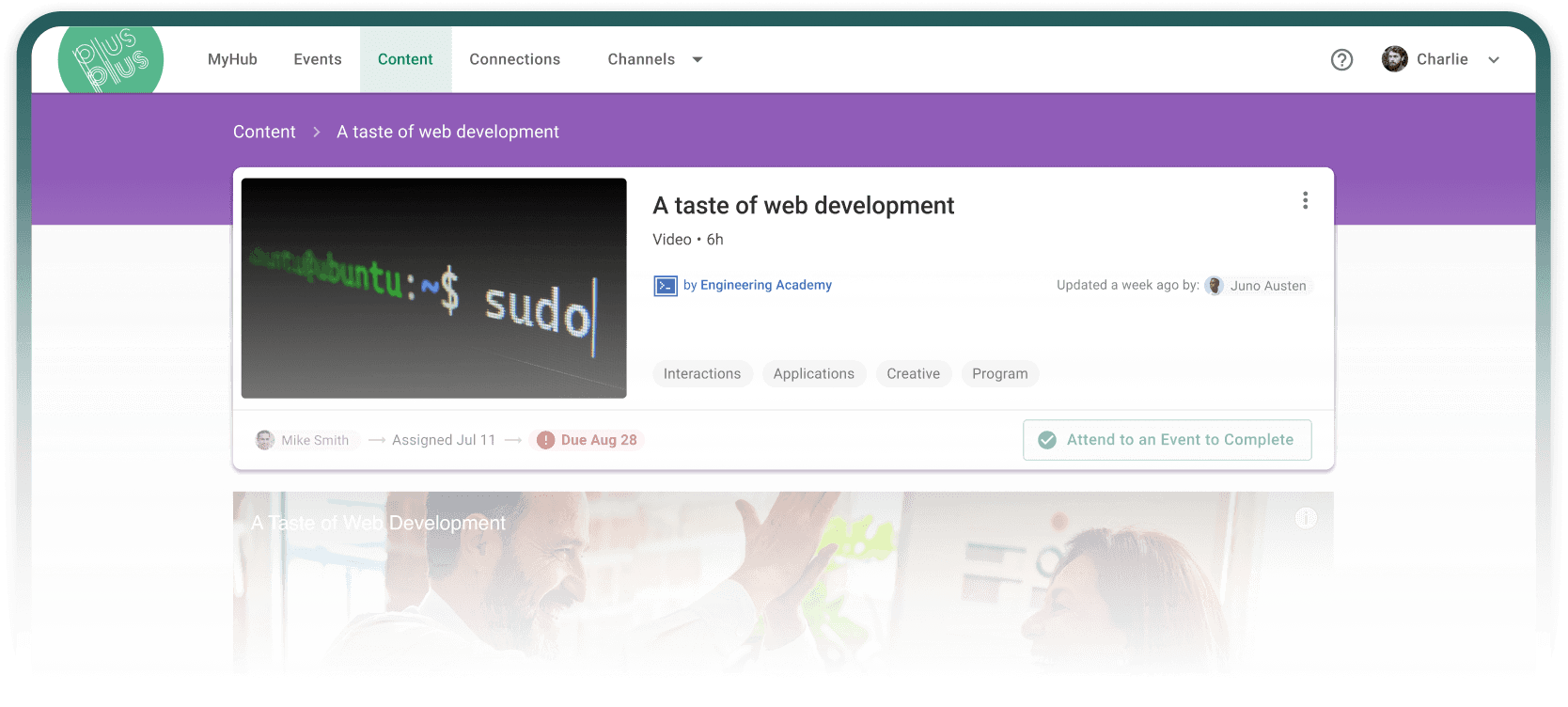
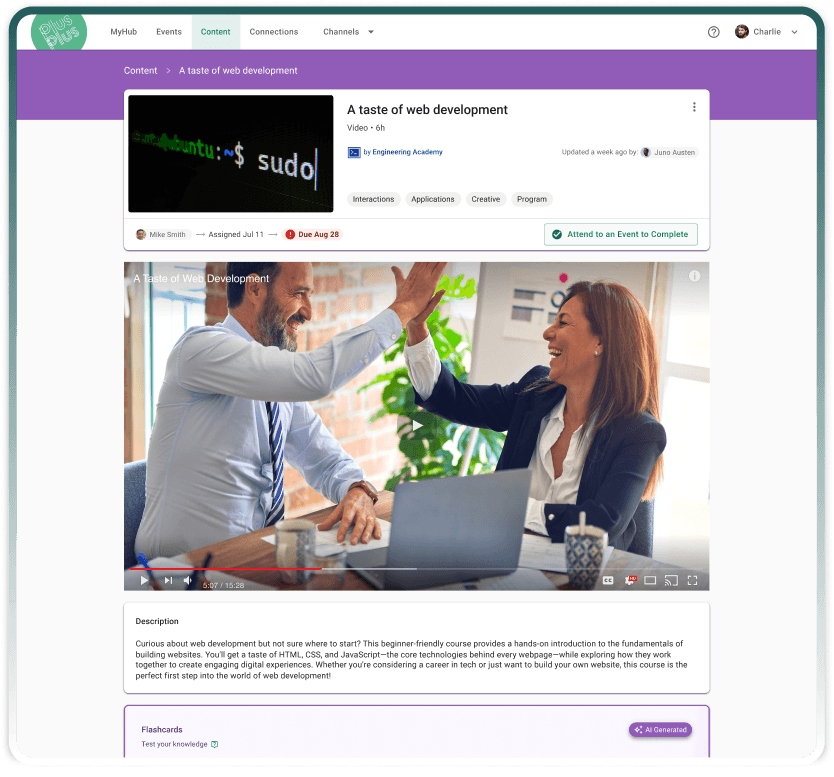
OnDemand Content
Create and curate content from any source.
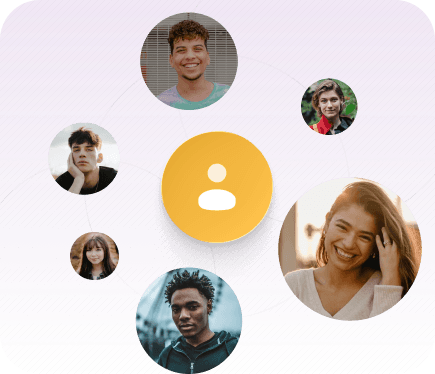
Expert Connections
Enable your people to connect with the experts who will help them to grow.
get started
Learn more about PlusPlus
35%
increase in revenue per employee
60
admin hours saved monthly
40%
monthly opt-in engagement rate
Benefits
LMS
Traditional Learning Platform
Functional Onboarding
Blended Tracks
Workflow Automation
Assessments
Native Surveys
Easy Authoring
Collaborative Learning
Blended Tracks
Workflow Automation
Easy Authoring
+
LXP
Informal Learning Platform
Leadership Development
Blended Tracks
Assessments
Native Surveys
Easy Authoring
Reporting
Mentorship & Coaching
Mentorship & Coaching
Expert Connections
Gamification & Social Learning
Knowledge Sharing
Gamification & Social Learning
My Hub
Easy Authoring
=
PlusPlus
Knowledge Sharing Platform
Compliance Training
Blended Learning
Live Events
Authoring Self-Paced eLearning
Workflow Automation
Reporting
Customer Enablement
Channels for Access Control
Flexible Content Sharing
Easy Authoring
Customer success story

Discover how PlusPlus delivers hundreds of learning programs to 18,000+ engineers with a single Program Manager
+ 1,000
An average of +1,000 monthly engagements by learning managers and content creators
3
A team of 3 are responsible for +10,000 technical engineers’s knowledge sharing
+ 10,000
Employee engagement with learning content soared to +10,000 interactions
Knowledge is already at your fingertips
blended learning programs with Tracks
No special skills or tools needed. Use all the learning content and people already at your disposal to create learning programs quickly.
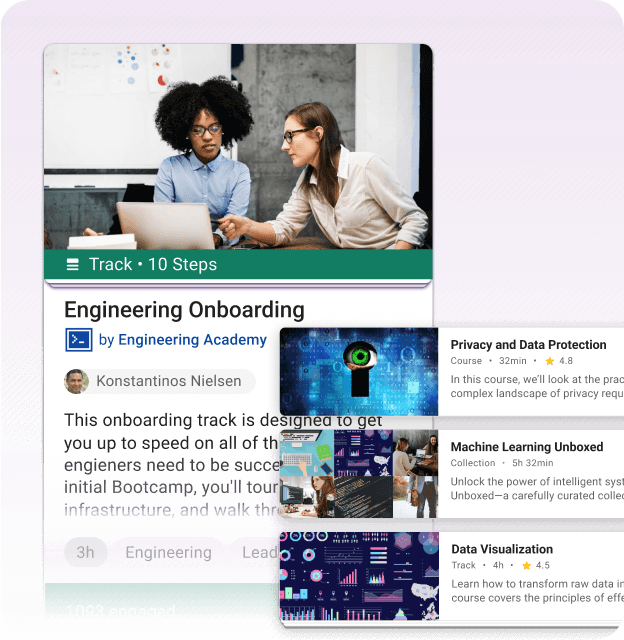
Why us
Why PlusPlus
We make learning social and easy to manage.
Cohort assignments
Effortlessly tailor learning programs to meet the needs of your teams.
Collaborative learning
Encourage active feedback and expertise sharing in the flow of learning.
Automated management
Streamline all administrative aspects of learning management.
Customize notifications
Automate notifications for assignments, enrollments, waitlists, and more across multiple channels.
Track attendance
Automatically synchronize attendance and assignment rosters with calendar invites via two-way integration.
Meet teams where they are
Boost engagement by delivering learning to teams and cohorts within existing workflows.
Unify data
Aggregate all of your learning data in a single platform for powerful, unified performance insights.
Connect securely
Securely automate data sharing between platforms via API, CSV export, in-app reporting, and more.
Consolidate tools
Reduce costs and simplify workflows by unifying your learning stack within a single platform.
Supported partnership
Our dedicated team of experts partner with you to be an extension of your team and deliver best-in-class customer service.
Customer success story

Learn how Netflix uses PlusPlus to boost engagement by 40%
+ 1,000
A small DevEd team of four supports learning for thousands of engineers
2x
Growth in internal training events after lowering creation barriers
100%
Internal workshops supported by standardized best-practice frameworks
max AI Agent
Max: Your Know-It-All AI Agent
Max is like an old-timer with all your internal know-how who you can ask anything.
Capture and Transcribe Knowledge
Max transcribes live conversations, workshops, and classes, making organizational knowledge easily accessible.
Intent-Based Search
Max uses semantic search to understand natural language queries and provide precise answers from your learning content.
Direct Answers
Max offers immediate answers to your questions, saving you from sifting through documents or recordings.
case studies
Assist: Your Learning Management Assistant
We make learning social and easy to manage.

Capture and Transcribe Knowledge
Copilot suggests course descriptions and workshop titles based on context and content.
Participant Notifications
Copilot manages updates and notifications for participants, ensuring everyone stays informed.
Data Analysis
Copilot analyzes learning data, providing insights and visualizations to help communicate your learning program's impact effectively.
Customer success story

Explore how LinkedIn increases live workshop attendance by 600% with PlusPlus
6X
LinkedIn boosted engineering workshop attendance six-fold
40%
Opt-in engagement rate versus <5% industry standard
60 hrs
Saved ~60 administrative hours monthly with automation
Explore our Learning and Development Community, TechKnowCon.
Learn more about our growing Learning and Development community, TechKnowCon